13. Enhancing Security Measures
Date: 2023-01-16
Status
Accepted
Context
The necessity to bolster the security of our application has been identified, particularly in relation to the encryption of secret data during deployment.
Decision
Management of Secrets
To protect secret data during deployment, we have decided to utilize SOPS.
- For HELM, the helm-secrets plugin will be employed.
- For ArgoCD, we will integrate with Argo CD Integration.
The following diagram illustrates the process:
graph TD
A(GIT) -- Push --> B(GitLab CI/CD)
B -- Run --> C[Helm]
C -- Use --> D(helm secrets)
B -- Pul --> F[ArgoCD]
F -- Run --> G[Kubernetes]
G -- Run --> H[Service]
style A fill:#58c0f0,stroke:#333,stroke-width:2px
style B fill:#4caf50,stroke:#333,stroke-width:2px
style C fill:#f9a825,stroke:#333,stroke-width:2px
style D fill:#f9a825,stroke:#333,stroke-width:2px
style F fill:#f9a825,stroke:#333,stroke-width:2px
style G fill:#f9a825,stroke:#333,stroke-width:2px
style H fill:#f9a825,stroke:#333,stroke-width:2px
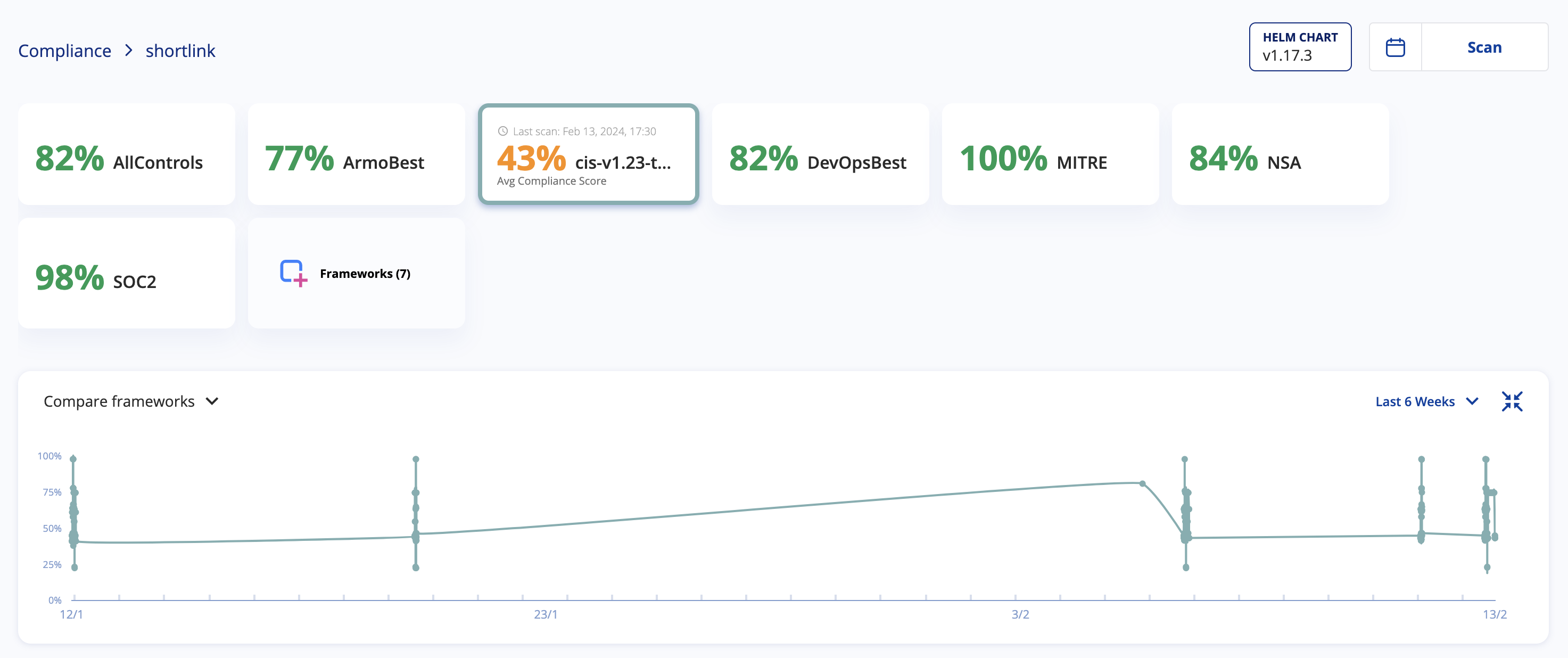
Security in Kubernetes
To identify potential security issues within our cluster, we will use kubescape.
Supply Chain Security
To ensure the security of our supply chain, we will adopt SLSA. For docker builds, the flags --sbom=true and --provenance=true will be added.
Consequences
- The use of SOPS will be required to decrypt secret data prior to deployment.
- Kubescape will be used to regularly scan our cluster for potential security issues.
- SLSA will be adopted to ensure the security of our supply chain.